A constant eye on the vehicle fleet
No matter how high the level of protection against cyberattacks established during development, it will inevitably diminish over the course of the vehicle’s service life.

For that reason, vehicles and vehicle fleets will require an active, ongoing security approach in the future, which monitors known risks and attack vectors and also identifies and mitigates new risks. Especially because when the risk management throughout the vehicle life cycle.
It takes examination of several areas and action on several levels to obtain a meaningful picture of the overall threat situation. Two key components are required: first, embedded in-vehicle attack detection in the form of an Security Operations Center (SOC) in the backend, where the attacks are aggregated and evaluated to prevent scaling of attacks across the entire fleet.
Intrusion detection in the vehicle
In-vehicle intrusion detection systems serve to detect external attacks (via remote connectivity) at an early stage, to detect manipulation of systems relevant to driving (e.g. steering system, engine control), and to detect manipulation attempts via easily accessible interfaces (e.g. the diagnostic interface).
- A network-based IDS for the CAN bus monitors the CAN traffic and analyzes it using a rule-based method. The IDS detects typical CAN attack signatures as well as anomalies that indicate previously unclassified attacks.
- A host-based IDS on the connectivity ECU monitors the integrity of the operating system and applications, among other things. It recognizes changes in system and application files and scans outgoing and incoming network connections.
- A combination of host-based and network-based IDSs ultimately creates a hybrid/distributed IDS that improves coverage of the vulnerabilities in the vehicle and provides comprehensive information about the approach the attackers take.
Another important advantage of an in-vehicle IDS is that rather than sending all the data traffic and large logs to the backend, it reports only the discovered anomalies. This dramatically reduces the bandwidth requirements for the transmission of security monitoring information.
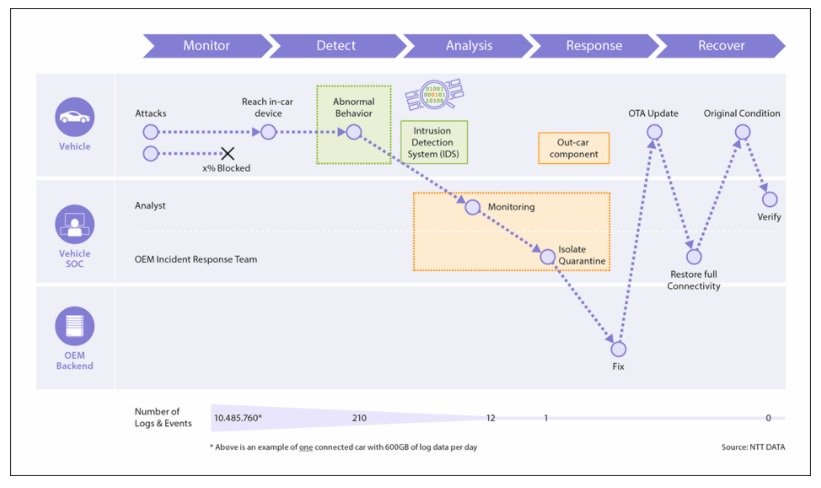
Figure 1: Security incident management for the vehicles follows a cycle of monitoring, attack detection, analysis, and response. The in-vehicle IDS dramatically reduces the bandwidth requirements for transmitting security monitoring information. ( NTT Security, ESCRYPT)
V-SOC: synthesis of SIEM and security analysts
The security events from the entire fleet as communicated by the in-vehicle IDS and further data relevant to IT security from the connected automotive ecosystem ultimately come together in a Vehicle Security Operations Center (VSOC) in the backend. Here, the Security Incident and Event Management (SIEM) solution serves as a central tool that starts by analyzing incoming IT security events – automatically and in real time. This involves the SIEM searching for certain predefined attack patterns and combing its database for related symptoms. In doing so, it precisely and reliably identifies known attacks, can display them via a dashboard, and can even develop its own models using machine learning functionalities. However, SIEM solutions are less suitable for detecting new and unknown intrusion scenarios. Especially since automotive security environments – with components that are specially developed for the vehicle platform – still have no standard vulnerability management solutions that could be directly connected up and used with SIEM.
For that reason, in addition to the technical implementation of a SIEM solution, the connected vehicle fleet requires specialized technical and content-related functionalities. One of these is threat intelligence, which systematically evaluates sources describing new attacks and attack methods, derives indicators of compromise from the existing data, and searches specifically for symptoms of these new attack techniques. It also needs security analysts, which are an absolutely essential component of the VSOC. With their expertise in the automotive security domain, they search specifically for new threats and track them in the log databases (threat hunting). The security analysts can uncover and outline the next potential steps in the attack path (e.g. lateral movements) and can enhance the analysis methods of SIEM and the IDS sensors. This way, they will be able to automatically detect threat scenarios in the future or retrospectively check the fleet for attacks that have already occurred.
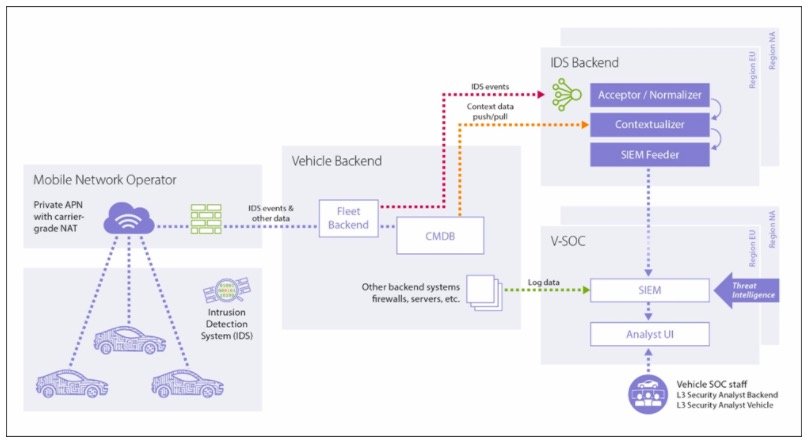
Figure 2: Components of a holistic Vehicle Security Monitoring – From intrusion detection to the Vehicle Security Operations Center. ( ESCRYPT)
Alert validation and globally distributed security structures
A good VSOC should supply fleet operators with actionable information, i.e. information about an existing or imminent threat that enables them to develop, test, and roll out suitable countermeasures. One of the greatest challenges here is alert validation, i.e. distinguishing between “false-positive” and “real” problems. To enable the most valid, situationally effective, and correct assessment of potential attacks in the VSOC and prevent alert fatigue, the assets present in the connected vehicle fleet’s overall system (classic ECUs, domain controllers, actuators, sensors, etc.) should be automated to the highest degree possible and the greatest possible amount of integrated information should be available from the OEM or fleet operator (current software inventories and hardware components in the vehicle, repair-shop visits, etc.). Alert validation and the security analysts’ ability to train a machine-learning system to differentiate between alerts are hallmarks of the VSOC’s quality.
Another important point is that OEMs and operators of large, globally distributed fleets will achieve the required reliability and resilience only if they have access to distributed Security Operations Centers in different regions. First and foremost, this will enable them to comply with the various country-specific legal requirements (e.g. with regard to data protection) and to furnish the licensing and regulatory authorities with proof at any given time that they have an appropriate risk management system in place for their fleets in the field. A cost-effective way for them to do this is to make use of existing Security Operations Centers and best practices that are globally available for enterprise IT. These are already capable of adequately processing the high data volumes associated with fleet-wide attack detection while implementing a level of protection that meets the requirements of the new security regulation and covers the vehicle’s entire service life.
www.escrypt.com

